What is the DORA Regulation and Why Does It Matter?
- Vignesh Prem
- Jan 20
- 9 min read
The DORA regulation, or Digital Operational Resilience Act, is a binding EU framework ensuring the financial sector can withstand severe operational disruptions. It establishes a unified rulebook for ICT risk management, incident reporting, resilience testing, and third-party risk, making sure banks, insurers, and critical tech providers can survive a major digital crisis.
What makes the DORA regulation a game-changer for financial resilience?
The DORA regulation is a fundamental shift because it replaces a patchwork of national rules with a single, harmonized EU-wide standard. It moves the goalposts from simply preventing cyberattacks to proving that your organization can maintain critical functions when things go wrong, elevating technology risk management to a board-level imperative.

The core mission is to guarantee the financial system's continuity. DORA is not just another compliance checkbox; it's a blueprint for digital survival.
What are the five pillars of DORA?
DORA is built on five interconnected pillars that form a complete resilience framework. To achieve compliance, your organization must master each one: ICT Risk Management, Incident Reporting, Digital Operational Resilience Testing, ICT Third-Party Risk Management, and Information & Intelligence Sharing.
Here’s a quick rundown of what they demand:
DORA Pillar | Key Requirement | Primary Business Impact |
|---|---|---|
ICT Risk Management | Establish a comprehensive framework to identify, protect, detect, respond to, and recover from all ICT risks. | Elevates IT risk to a strategic board-level responsibility, requiring integrated governance and controls. |
Incident Reporting | Standardize the classification and reporting of all major ICT-related incidents to regulatory authorities. | Demands streamlined, rapid communication processes and greater transparency during a crisis. |
Digital Operational Resilience Testing | Regularly test all ICT systems and defenses using a variety of methods, including advanced threat-led penetration testing (TLPT). | Mandates a proactive, continuous testing culture instead of periodic, compliance-driven checks. |
ICT Third-Party Risk Management | Impose strict rules for managing risks from third-party ICT providers, especially cloud services. | Makes vendor and supply chain oversight a critical function, with direct accountability for partner resilience. |
Information & Intelligence Sharing | Encourage the sharing of cyber threat information and intelligence with other financial entities to build collective defense. | Fosters a collaborative security environment, moving organizations from isolated defense to community-based resilience. |
The clock is ticking. A recent study found that a staggering 96% of financial services organizations in the EMEA region believe they need to make significant changes to comply by the January 17, 2025, deadline. This isn't a minor tweak—it's a major operational overhaul.
As you navigate these complex requirements, you might find our guide on top GRC frameworks useful for contextualizing DORA.
How do you determine if DORA applies to your organization?
To determine if the DORA regulation applies, you must assess if your organization is part of the EU's financial ecosystem. The regulation’s reach is broad, covering not just traditional financial institutions but also the critical technology partners they depend on, ensuring every part of the financial system is resilient.
Which entities fall under DORA's scope?
DORA casts a wide net, pulling in a huge range of businesses. Your organization is almost certainly in scope if it’s one of the following:
Traditional Financial Institutions: Credit institutions, investment firms, and insurance companies.
Payment and E-money Institutions: Businesses that process payments or issue electronic money.
Asset Management and Funds: Managers of alternative investment funds and UCITS.
Critical Third-Party ICT Providers: Key technology vendors like cloud service providers, core banking software vendors, and data analytics firms whose services are essential to financial operations.
For the first time, major tech suppliers face direct oversight from financial regulators, making them as accountable as the banks they serve.
How does DORA's principle of proportionality work?
DORA uses "proportionality," meaning its rules scale based on your organization's size, risk profile, and systemic importance. A small regional credit union won't face the same grueling testing standards as a global investment bank. This practical approach makes compliance more manageable by tailoring the burden to the risk.
A clear assessment of your risk profile is the foundation for your entire compliance effort and a cornerstone of any solid compliance risk management strategy. Understanding your specific obligations under the DORA regulation is the first step. At DataLunix.com, we specialize in helping organizations right-size their compliance journey.
What are the details of DORA's five core pillars?
To master the DORA regulation, you must understand its five interconnected pillars, which create a tough digital resilience framework. These principles will reshape daily operations, from risk assessments to vendor contracts, moving your team from a reactive checklist mindset toward a proactive culture of resilience.
Let's break down each pillar.

What does the ICT risk management pillar require?
This pillar requires a comprehensive and well-documented ICT risk management framework owned and approved by the management body. The goal is to build a system that can identify, protect, detect, respond to, and recover from all ICT-related risks, embedding resilience by design through solid governance and clear policies. Our team’s deep expertise in governance, risk management, and compliance is often where our clients start.
How does DORA change incident reporting?
DORA standardizes how you handle digital disruptions by forcing you to focus on how quickly and transparently you report incidents. It introduces consistent reporting thresholds and deadlines across the EU, requiring a streamlined process to detect, classify, and report major incidents within tight timeframes. This requires seamless integration between your security and ITSM platforms.
Why is resilience testing so important under DORA?
DORA makes continuous, rigorous testing mandatory, moving beyond occasional vulnerability scans. You must proactively and consistently test your defenses to prove they can hold up against sophisticated attacks.This includes:
Vulnerability assessments and scans
Network security assessments
Physical security reviews
Threat-Led Penetration Testing (TLPT) for critical entities
Findings must be used to actively fix weaknesses, creating a constant cycle of testing and improvement at the heart of the DORA regulation philosophy.
How does DORA govern third-party risk?
DORA holds you directly accountable for the resilience of your critical ICT vendors, operating on the principle that you are only as resilient as your weakest supply chain link. To tackle these requirements, organizations can use a detailed guide to building a Third-Party Risk Management (TPRM) framework. Key mandates include performing serious due diligence, ensuring contracts have specific resilience clauses, and mapping out clear exit strategies.
What role does information sharing play in DORA?
The final pillar encourages financial entities to exchange cyber threat information and intelligence within trusted communities. The idea is to build a collective defense for the entire sector. Instead of fighting threats in a silo, you become part of a network that shares insights to raise the security bar for everyone. DataLunix.com helps organizations implement the systems needed to join these crucial information-sharing circles securely.
What are the key compliance timelines and milestones for DORA?
Achieving compliance with the DORA regulation is a marathon with firm deadlines, making a clear roadmap essential. The regulation came into force with a two-year implementation window, giving organizations time to conduct gap analyses, overhaul processes, and implement the necessary controls to meet DORA’s tough standards by the final enforcement date.
What are the key dates your organization must know?
Missing these milestones could lead to regulatory penalties. Here’s a simple breakdown of the DORA timeline:
January 16, 2023: The DORA regulation was published and became law, starting the 24-month preparation window.
January 17, 2025: The final deadline. By this date, all affected organizations must be fully compliant.
Ongoing Post-2025: National competent authorities will begin conducting rigorous audits and inspections to ensure sustained compliance.
The period until January 2025 is an active implementation window. Organizations that haven't started their gap analysis are already falling behind.
What should your organization have done by now?
You should be well past the "awareness" stage. A prepared organization should have already completed these key activities:
Completed a Scope Assessment: Definitive answer on whether DORA applies and which specific rules are most relevant.
Conducted a Gap Analysis: A thorough comparison of your current frameworks against DORA's demands.
Established a DORA Project Team: A dedicated, cross-functional team with executive backing is in place.
Developed a Remediation Roadmap: A detailed, prioritized roadmap with clear milestones pointing to the January 2025 deadline.
If you are lagging, it’s time to act fast. Partnering with a specialist like DataLunix.com can help you quickly move from assessment to active remediation.
How does DORA reshape IT operations and service management?
The DORA regulation is a hands-on mandate that will fundamentally change the day-to-day reality for your IT teams. It forces a major shift: managing services is no longer enough. Your IT Service Management (ITSM) and IT Operations Management (ITOM) frameworks must evolve to become your primary evidence for demonstrating resilience to regulators.
How will DORA affect incident management?
DORA’s strict incident reporting timelines mean your current workflows likely won't cut it. The regulation demands a swift, standardized response that requires re-engineering your ITSM tool to automate the process.Key changes include:
Automated Classification: Incidents must be instantly categorized based on DORA’s specific criteria.
Pre-defined Escalation Paths: Workflows must route major incidents to the right teams without delay.
Integrated Reporting: Your system must generate regulatory reports directly from the incident record.
Manual handoffs and fuzzy processes create unacceptable risks under DORA. Your ITSM platform must become the single source of truth.
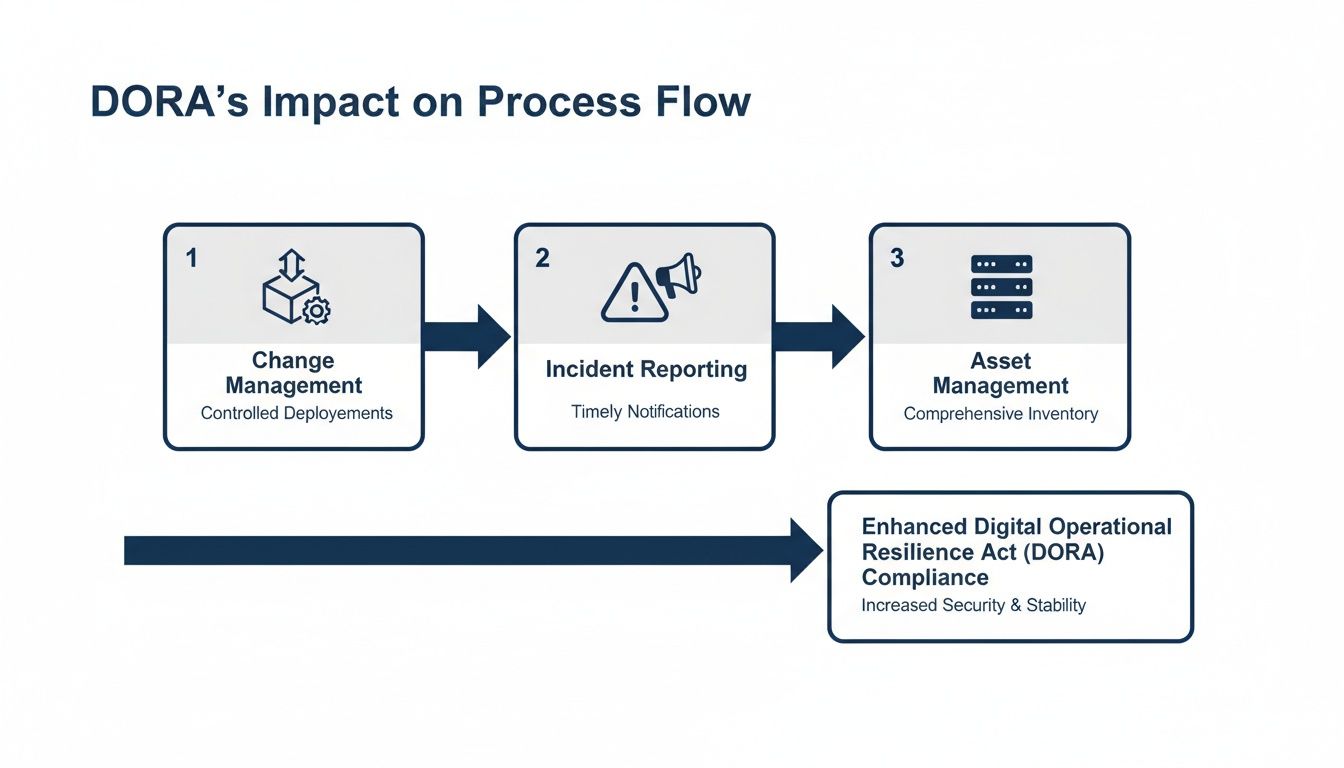
Why is asset management now critical for compliance?
DORA elevates IT Asset Management (ITAM) to a mission-critical compliance activity. You must have a perfect, real-time inventory of all hardware and software assets, especially those from external vendors, to map operational dependencies and assess supply chain risk. An accurate Configuration Management Database (CMDB) is non-negotiable for demonstrating control over third-party risks, a process we break down in our comprehensive guide to ServiceNow IRM modules.
How will change management and resilience testing align?
DORA's mandate for continuous resilience testing directly impacts your change management process. Every software release or infrastructure update must be evaluated for its potential impact on operational resilience before going live. This forces tighter integration between your change advisory board (CAB) and security testing teams, adding a mandatory quality gate to your deployment pipeline. DataLunix.com specializes in embedding these resilience checks into existing ITSM workflows.
How can you build an actionable roadmap to DORA readiness?
Getting compliant with the DORA regulation is manageable with a structured, five-stage roadmap. This practical journey guides you from initial assessment to sustained resilience, providing a blueprint for a successful project by weaving resilience principles directly into your core operational workflows.
Stage 1: How do you scope your unique obligations?
First, you need to define exactly what the DORA regulation means for your organization. Map the regulation's mandates against your specific business operations, risk profile, and third-party dependencies to ensure your efforts are laser-focused from day one.
Stage 2: How do you conduct a gap analysis?
Once you know what’s required, a thorough gap analysis compares your current ICT risk framework and processes against DORA’s mandates. The output is a clear, prioritized list of vulnerabilities and non-compliant processes that need fixing, informing your entire remediation strategy.
Stage 3: How do you map and remediate controls?
With your gaps identified, the next step is to design and implement the necessary controls to close them. This is the heavy-lifting phase where policies are rewritten and workflows are re-engineered. A critical piece is shoring up your ICT third-party risk management; the ultimate due diligence questionnaire guide is an excellent resource here.
Stage 4: How can you automate evidence collection?
Automate the soul-crushing task of manually gathering audit evidence. By integrating your GRC platform with your ITSM and security tools, you can create a system that automatically collects the proof needed to demonstrate compliance, saving hundreds of hours and ensuring you’re always audit-ready.
Stage 5: How do you establish continuous testing?
DORA compliance is not a one-time project. You must establish a continuous cycle of testing, monitoring, and improvement, including regular vulnerability scans and penetration testing. This constant vigilance, similar to what we detail in our guide to ServiceNow compliance, ensures your organization stays resilient as threats evolve.
Frequently Asked Questions About DORA
What is the main goal of the DORA Regulation?
The main goal of the DORA regulation is to create a unified, high standard for digital operational resilience across the EU financial sector. It aims to ensure that every bank, insurer, and investment firm can withstand, respond to, and recover from severe ICT disruptions without causing systemic instability.
Does DORA apply to cloud service providers?
Yes, absolutely. The DORA regulation brings critical third-party ICT providers, including major cloud services like AWS, Microsoft Azure, and Google Cloud, under direct supervision by European authorities. This is a major shift that makes the tech supply chain directly accountable.
How is DORA different from other cybersecurity rules?
While older rules focused on preventing attacks, the DORA regulation assumes disruptions will happen. Its focus is on proven resilience—the ability to maintain critical functions during a crisis. Unlike previous national guidelines, DORA is a single, legally binding standard for the entire EU.
What are the penalties for non-compliance?
Firms that fail to comply with DORA face significant penalties, including fines of up to 1% of the average daily worldwide turnover from the previous business year. National regulators have the authority to impose these periodic payments, creating a powerful incentive to get compliance right.
When preparing for a regulation as complex as DORA, having an expert guide is crucial for success. For organizations seeking a trusted partner, DataLunix.com provides specialized readiness assessments and implementation services, turning the challenge of DORA compliance into a strategic advantage in operational resilience. Start your DORA compliance journey with a DataLunix expert today.


