How Can You Build a Robust 3rd Party Risk Management Program?
- Feb 8
- 13 min read
A robust 3rd party risk management (TPRM) program is the continuous process of identifying, assessing, and neutralizing risks associated with your external vendors. It involves a structured lifecycle from due diligence and onboarding to continuous monitoring and secure offboarding, ensuring your partners don't introduce unacceptable security threats.
Why is 3rd Party Risk Management a core business function?
TPRM is a core business function because every third-party partner represents a potential entry point for threats. A solid 3rd party risk management program acts as your vetting system, ensuring you only partner with vendors who meet your security standards, thereby protecting you from data breaches, operational disruptions, and reputational damage.
This isn’t just about ticking a compliance box. It’s a fundamental part of modern business resilience. A security failure at one of your vendors can directly translate into a breach of your own systems, crippling downtime, or a PR nightmare that damages your reputation.
How is TPRM evolving in the GCC and Europe?
In the GCC and Europe, TPRM is becoming critical as digital transformation accelerates, expanding the potential attack surface through complex supply chains and cloud services. The numbers prove it: the Middle East and Africa TPRM market hit USD 0.17 billion in 2023 and is projected to grow at a 17.1% CAGR through 2030.
Effective TPRM is your shield against several major threats:
Data Breaches: It stops unauthorized hands from getting to sensitive customer or company data that your vendors hold.
Operational Disruptions: It ensures a glitch at a key supplier doesn’t bring your own business to a screeching halt.
Reputational Damage: Your brand’s image is protected from being tarnished by a partner's security mistake or unethical conduct.
Regulatory Penalties: It keeps you on the right side of tough data protection laws like GDPR in Europe and various national regulations across the GCC.
A proactive TPRM program flips the script on risk. Instead of reacting to disasters, you build a strategic advantage that fosters trust with customers, partners, and regulators alike. It's a clear signal that you’re serious about protecting data and staying compliant.
Ultimately, managing third-party risk is just good governance. To get it right, you need to go deep, and resources like this comprehensive guide to third-party risk management are a great starting point. To see how TPRM fits into the bigger picture, check out our guide on building a GRC (Governance, Risk, and Compliance) framework that actually works.
What are the stages of the TPRM lifecycle?
A solid 3rd party risk management program is a continuous cycle, not a one-time audit, that protects your organization throughout the entire vendor relationship. Following a structured lifecycle—from initial vetting and contracting to ongoing monitoring and final offboarding—turns a massive undertaking into a manageable, repeatable process that strengthens your security posture.
This process flow maps out the core stages of identifying, assessing, and neutralizing vendor risks.
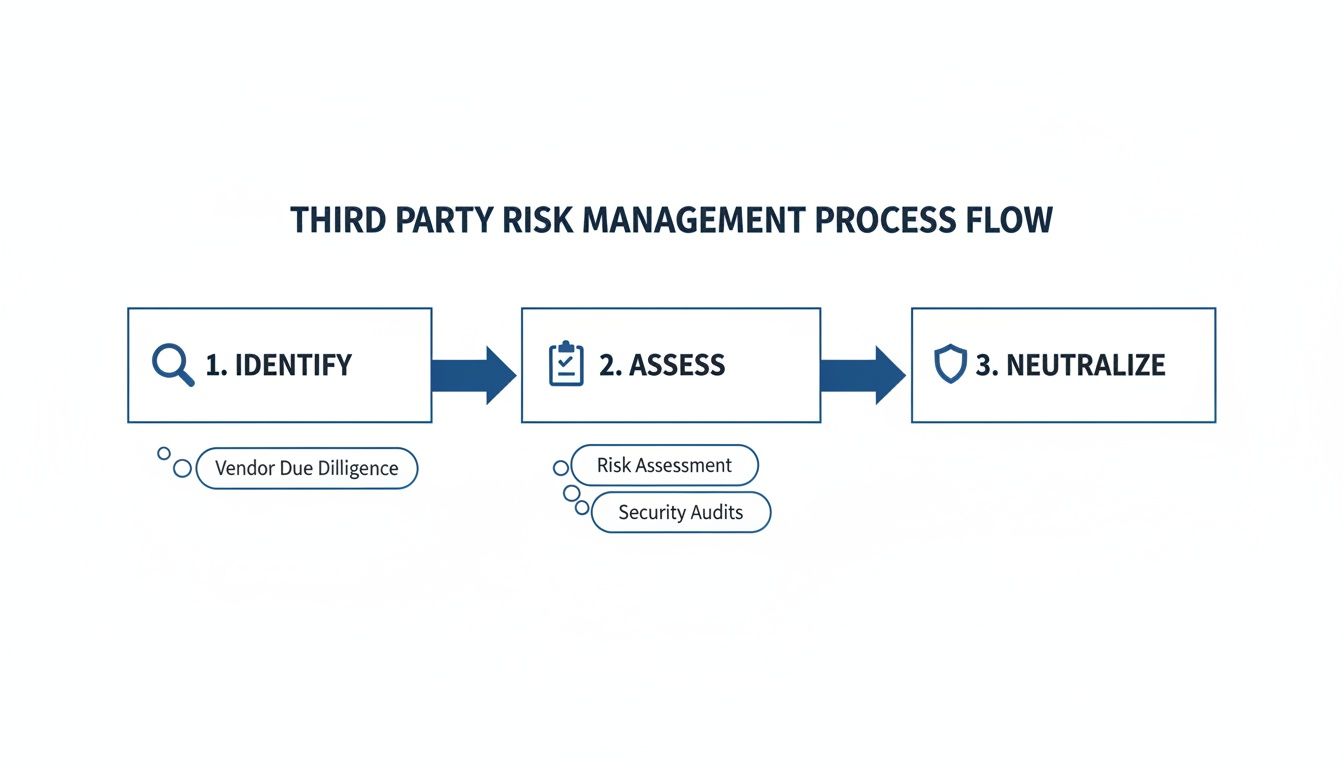
The key takeaway? TPRM is an active discipline, not a passive one. It demands a clear progression from initial vetting to ongoing mitigation, where each stage builds on the last to create a comprehensive defense.
What is the due diligence and selection stage?
The due diligence stage involves thoroughly vetting a potential vendor's security and compliance posture before signing a contract. It's the essential background check to confirm if a vendor is trustworthy enough to handle your data or support your operations, preventing future security incidents by starting with a secure foundation.
Think of it as the interview process for a critical new hire. You wouldn’t give someone the keys to your most sensitive information without first checking their references and understanding their capabilities. Rushing this step is a classic mistake that almost always leads to bigger problems down the road.
The main goal is to gather enough hard evidence to make an informed risk decision. This means using a few different assessment angles.
Security Questionnaires: Send out standardized assessments (like SIG Lite, CAIQ, or HECVAT) to get a clear picture of a vendor's internal controls.
Documentation Review: Get your hands on their SOC 2 reports, ISO 27001 certifications, and recent penetration test results.
External Scanning: Use security rating tools to get an objective, outside-in view of their security posture.
How should you handle contracting and onboarding?
Once due diligence is complete, you must embed security and risk management requirements directly into the contract. This isn't just a legal formality; it's a strategic control that legally formalizes expectations, defines accountability for data protection, and establishes clear rules for the entire relationship, including breach notifications.
A well-written contract is your rulebook for the relationship, defining everything from service level agreements (SLAs) to breach notification protocols. Without these clauses, you have very little recourse if a vendor fails to meet your security standards.
Key contractual elements to nail down include:
Data Protection Clauses: Specify exactly how your data should be handled, stored, and processed.
Right to Audit: Make sure you have a clause that gives you the right to assess the vendor's controls yourself.
Breach Notification Timelines: Define precisely how and when they must report a security incident to you.
Secure Offboarding Requirements: Outline the exact process for data return or destruction when the contract ends.
Onboarding then becomes about integrating the vendor into your systems safely, granting only the absolute minimum access (least privilege principle) they need to do their job.
Why is continuous monitoring essential?
Continuous monitoring is the ongoing process of tracking a vendor's security posture throughout the contract lifecycle. It is essential because a vendor's risk profile is not static; it can change overnight due to new vulnerabilities or internal changes. This stage transforms TPRM from a periodic check-up into a dynamic, real-time defense.
Continuous monitoring transforms TPRM from a periodic check-up into a dynamic, real-time defense system. It allows you to spot emerging threats and address them before they can be exploited.
Effective monitoring uses a mix of automated tools and periodic reviews:
Automated Security Ratings: Track the vendor's external attack surface for any new risks that pop up.
Threat Intelligence Feeds: Monitor for news of breaches or vulnerabilities that might affect your vendors.
Annual Re-assessments: Re-validate their controls to ensure they still meet your requirements.
For a deeper look into how modern platforms can automate these processes, check out our ServiceNow IRM guide which covers TPRM modules and what they can do.
What does secure offboarding involve?
Secure offboarding is the final, structured process of ending a vendor relationship to ensure all access is revoked and your data is securely returned or destroyed. Neglecting this step leaves behind "ghost" access points and orphaned data, creating security risks that can linger for years and violate compliance requirements.
Just as onboarding needs to be deliberate, offboarding has to be just as methodical. Failing to properly close out a relationship is like forgetting to get the keys back from a former employee. A formal checklist ensures nothing gets missed.
Critical offboarding steps include:
Revoke All Access: Terminate every user account, API key, and network connection. No exceptions.
Confirm Data Disposition: Get confirmation that all your data has been securely returned or verifiably destroyed according to the contract.
Finalize Financials: Settle all outstanding invoices and close out all financial ties.
Update Inventories: Remove the vendor from your central inventory and risk register to keep your records clean and accurate.
How do you navigate key TPRM regulations in the GCC and Europe?
Navigating 3rd party risk management regulations in the GCC and Europe is non-negotiable, as getting it wrong leads to steep financial penalties and severe reputational damage. Building your TPRM framework around these legal mandates is a proactive stance that ensures compliance, builds trust, and makes your business more resilient.
Think of these rules less as a burden and more as a blueprint. When you build your TPRM framework around these legal mandates, you’re not just ticking a compliance box. You’re building a fundamentally more secure, trustworthy, and resilient business. It’s a proactive stance that helps you get ahead of regional threats and keep stakeholders confident.
What is GDPR and how does it impact vendors?
The General Data Protection Regulation (GDPR) is Europe's landmark data privacy law that holds you, the "data controller," responsible for how your third-party vendors, or "data processors," handle EU residents' personal data. This means if your vendor has a breach involving your data, you are ultimately liable.
This shared legal responsibility completely changes how you manage vendors. You have to kick the tires and conduct serious due diligence to ensure your partners can meet GDPR's tough standards. This includes making sure they are:
Implementing appropriate technical and organizational measures to keep data safe in a way that matches the risk.
Notifying you without undue delay the moment they discover a personal data breach.
Gaining your written authorization before they bring in any sub-processors (your fourth parties).
When trying to get a handle on this, a practical AI GDPR compliance guide can be a lifesaver for understanding your obligations and protecting your data.
What are the key GCC data protection laws?
The GCC regulatory landscape is rapidly evolving with laws like the UAE's and Saudi Arabia's Personal Data Protection Laws (PDPL). These frameworks, inspired by GDPR, impose strict duties on data controllers and processors, making rigorous vendor cybersecurity controls and clear contractual agreements an absolute necessity for compliance.
Third-party supply chain breaches have become a massive driver for TPRM in the Middle East and Africa. The UAE is at the epicenter, thanks to its rapid push for digitalization. A recent report paints a stark picture: the region accounts for 2.1% of global entities but suffers 1.7% of breaches, with a worrying 28.6% of those traced back to a third party.
Beyond these sweeping data protection laws, you also have to watch out for sector-specific rules. Financial services in the UAE and KSA, for example, answer to central bank regulations that require intense cybersecurity and third-party risk checks. This layered regulatory environment means a unified approach to compliance and risk management isn't just a good idea—it's essential for survival. At DataLunix.com, we specialize in helping organizations build frameworks that handle these diverse requirements without missing a beat.
How do you build a TPRM governance framework?
A solid 3rd party risk management program lives or dies by its governance framework. It’s the constitution for your entire risk strategy, clarifying roles, decision-making processes, and the standards every vendor must meet. This framework turns scattered checklists into a cohesive, disciplined function that actively protects the business.
This framework lays down the law. It clarifies who does what, how decisions get made, and the standards every vendor relationship must meet. It’s the difference between ad-hoc panic and a repeatable, defensible process.
How do you define roles and responsibilities?
To build a TPRM framework, you must first assign clear ownership for every part of the vendor lifecycle using a RACI (Responsible, Accountable, Consulted, Informed) matrix. When everyone knows their specific role—from business owners to IT and legal—ambiguity is eliminated, critical tasks don't get dropped, and accountability is ensured.
Business Owners: They’re Responsible for kicking off the vendor relationship and managing it day-to-day. The need starts with them.
Procurement/Sourcing: They are Accountable for getting the contracts right, ensuring all the necessary security and compliance language is baked in from the start.
IT/Security Teams: These folks are Accountable for the heavy lifting of technical due diligence and keeping an eye on vendors’ security posture over time.
Legal & Compliance: They need to be Consulted to make sure vendor activities and contracts don't run afoul of regulations.
Senior Leadership: They’re kept Informed on the big-picture risks and how the program is performing, so there are no surprises.
Why is vendor tiering and risk appetite crucial?
Vendor tiering and a defined risk appetite are crucial because not all vendors pose the same level of risk. This strategy allows you to focus your most intensive due diligence on high-risk vendors (like data processors) while applying lighter scrutiny to low-risk suppliers, optimizing resources and preventing critical threats from being overlooked.
Your risk appetite statement is your north star for making tough calls. It's a formal declaration of how much risk you’re willing to take on to meet your goals. For instance, you might decide on a "zero tolerance" policy for any vendor that handles sensitive PII without proper certifications.
A smart vendor tiering strategy lets you point your most powerful microscope at your highest-risk relationships. This is the heart of modern 3rd party risk management—putting your energy where the biggest threats are.
If you’re building this from scratch, it helps to see how it fits into a larger structure. For a detailed playbook, check out our guide on how to build a GRC (Governance, Risk, Compliance) framework that actually works. DataLunix.com helps organizations get these fundamentals right every day.
What are the essential governance tools?
To make any of this work, you need two non-negotiable tools: a centralized vendor inventory and a comprehensive risk register. These aren't just spreadsheets; they are the single source of truth for your entire program. They’re what you’ll rely on for accurate reporting, smart decision-making, and proving compliance when auditors come knocking.
Ultimately, a strong governance framework isn't just a binder full of policies gathering dust. It's the engine that powers your TPRM program, making it a repeatable, defensible system that builds resilience against third-party threats for the long haul.
How do you unify TPRM with existing IT systems?
Effective 3rd party risk management shouldn't operate in a silo. The smart move is to plug your vendor risk program directly into your IT Service Management (ITSM) and IT Operations Management (ITOM) platforms, like ServiceNow. This integration breaks down walls, providing a unified view of your IT ecosystem.
This integration breaks down the walls, giving you a single, unified view of your entire IT ecosystem. When you connect these systems, TPRM stops being a periodic, box-ticking exercise and becomes a live, operational defense that massively improves your company’s resilience.
How does integration create a unified defense?
Connecting TPRM with ITSM/ITOM creates a unified defense by allowing risk data to flow directly to your operational teams. When a vendor has a breach, an integrated system can automatically generate a high-priority incident ticket in your ITSM tool, giving your IT team the immediate context needed for rapid response.
This seamless flow of information drives:
Faster Incident Response: IT teams can jump on vendor-related security events immediately, armed with all the context they need.
Proactive Problem Management: By overlaying vendor risk scores with performance data, you can spot troubling patterns and fix issues before they cause an outage.
Informed Change Management: If a change request involves a high-risk vendor, the system can automatically flag it for an extra layer of security review.
By connecting TPRM with operational platforms, you arm your frontline IT staff with the risk intelligence they need to make smarter, more secure decisions in real time. This operationalizes risk management in a way that static reports never can.
What are the practical benefits of a connected system?
The practical benefits of a connected system go beyond faster incident response. This approach creates a powerful feedback loop where vendor performance data from ITOM feeds back into the risk score, providing a more accurate assessment. This is especially vital in markets like the UAE, which dominates the regional TPRM market.
The region's explosive digitalization has cranked up vendor dependency, fueling demand for smarter TPRM solutions. Since 2021, large enterprises have been leading the charge, significantly ramping up their investment in both cybersecurity and dedicated TPRM platforms. You can dig into the regional market trends on Data Bridge Market Research.
Key advantages include:
Enhanced Visibility: A unified dashboard shows not just a vendor's risk score but also their active services, recent incidents, and performance SLAs.
Improved Efficiency: Automation slashes the manual work of toggling between systems, freeing up your teams to focus on actual risk mitigation.
Better Decision-Making: With a complete picture of a vendor's risk and operational impact, you can make much smarter calls on contract renewals and new partnerships.
At DataLunix.com, we specialize in building these unified ecosystems. Check out our guide on how you can unify GRC, governance, risk, and ITSM for your enterprise to build a truly connected defense.
How will AI power the future of TPRM?
The future of effective 3rd party risk management lies in AI and automation, which are essential for scaling programs beyond manual capabilities. These technologies transform TPRM from a reactive, checklist-driven chore into a proactive, predictive defense that can keep pace with modern threats by doing the heavy lifting human teams cannot.
This is about making your security program smarter and more scalable. AI-powered tools do the heavy lifting that human teams simply can't, completely changing how you spot, assess, and handle vendor risk.
How does AI proactively identify vendor risk?
AI proactively identifies vendor risk by continuously analyzing vast amounts of data to flag potential issues in real time, long before they become incidents. Instead of relying on static assessments, AI-powered engines can scour the internet and dark web for data leaks or signs of a compromised system related to your vendors.
These systems can:
Analyze a vendor's digital footprint to spot unpatched systems or poorly configured cloud assets.
Scan for breach chatter on hidden forums and social media that might signal an upcoming attack.
Predict which vendors are most likely to face a security incident based on their current security posture and industry trends.
What is predictive risk analysis?
Predictive risk analysis uses machine learning algorithms to forecast future threats by analyzing historical data and current security trends. This allows you to move beyond reacting to known issues and instead focus resources on vendors who pose the greatest future risk, preventing incidents before they occur.
This forward-looking capability is the core of a modern 3rd party risk management program. It lets you make strategic decisions based on data-driven predictions, not just past performance, fundamentally changing how you protect your organization.
How can automation streamline TPRM workflows?
Automation streamlines the entire TPRM lifecycle by eliminating manual bottlenecks and freeing up your security team to focus on strategic risk mitigation. AI-driven platforms can automate repetitive but critical tasks like analyzing security questionnaires, identifying risky contract clauses with NLP, and ensuring continuous compliance monitoring against regulations like GDPR.
Key automated workflows include:
Automated Questionnaire Analysis: AI can instantly review vendor security questionnaires, flagging inconsistent or risky answers that a human might miss.
Contractual Risk Identification: Natural Language Processing (NLP) can scan vendor contracts to pinpoint weak clauses related to data protection or breach notification.
Continuous Compliance Monitoring: Automation can track a vendor’s alignment with regulations like GDPR or regional laws, alerting you to any slip-ups.
At DataLunix, we build these intelligent, automated workflows directly into the IT systems you already use. By integrating AI-powered TPRM with platforms like ServiceNow, we create a unified and proactive defense that makes your risk management program more efficient, scalable, and intelligent.
Frequently Asked Questions about TPRM
What is the first step in building a TPRM program?
The first step in building a TPRM program is creating a complete, centralized inventory of all third-party vendors. You must know who your vendors are, what services they provide, and what data they access before you can manage their risk.
How is TPRM different from vendor management?
Vendor management focuses on procurement and performance, asking if a vendor is meeting SLAs and delivering value. In contrast, 3rd party risk management is a dedicated security function focused on a different question: "Is this vendor operating securely and protecting our data?"
How do you measure the ROI of a TPRM program?
The ROI of a TPRM program is measured by both quantitative and qualitative metrics. Quantitatively, it's seen in the reduced cost of third-party security incidents and breach avoidance. Qualitatively, the ROI appears as enhanced operational resilience, stronger customer trust, and a more secure brand reputation.
When you're ready to move beyond spreadsheets and build a resilient TPRM program integrated directly into your operations, DataLunix.com provides the expertise and solutions to unify your defenses. See how DataLunix strengthens your security posture.

